Crypto Thueves Dubbed ‘Rhleebear’ Run rules-scam rules

The cybercrime group called “Arriijaar” is accused of stealing more than $ 1 million by using what researchers say is one of the many Crypt Operations in the months.
Reports from Cylee Security Explains the Organized Campaign that includes malicious adverbs, malware, and payment websites – all under one network.
Extensions turned into rear steal tools
Instead of focusing on just one way, Hallbear includes many. According to the Koi Tuval Adoni security auditor, the party has sent more than 650 tools to its latest push.
This notes a sharp increase from its original functionality of the “Foxy Wallet” in July, including 40 Firefox extensions.
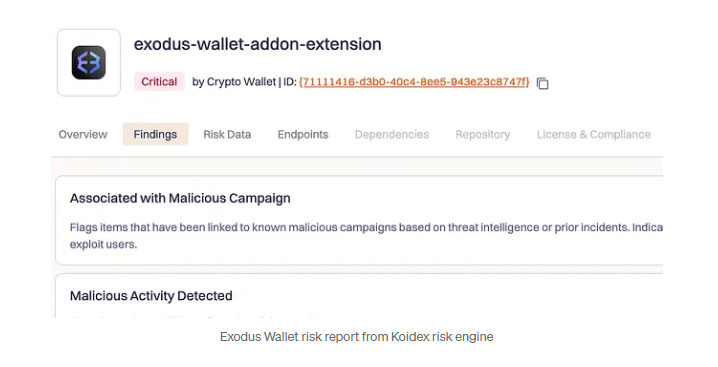
Group Plan, called “Extening Holokolological,” begins by publishing ads that look clean of Firefox such as video vendors or coordinates.
These extensions, issued under new publisher accounts, collect negative updates of the appearance. Later, the vicious versions added wallets such as metamask, TRONLINK, Klodus and the Rabro Fund.
When they are included, they capture the authenticity of the installation fields and send them to the control servers.

Malware is hidden in a nail software
The investigators also arrested about 500 negative files in the same group. Most of these are a well-known family Malwareware such as Lumstean, a cit in the same as Luca Dybar, and Trojons working as the sellers of other dangerous programs.
Distribution often occurs with Russian-language websites carrying broken or “rejected” software. Guide those who want free software, the attackers come far from the Crypto community.
Modular malware was also available for Koi safety, where the operator may add or change jobs without sending new files completely.
Fake Crypto services are designed to swing data
Based on reports, in addition to browser attacks and malware, the Haringbear has set up fraud and creams are ruined as real CryptCurrency solutions.
Some of these are said to donate Hardere Wallets, while others are a deception service for devices such as trzor.
And the offer is faket applications for good looking projects that show users in the filing phrases, independent buttons, and payment details.
Unlike standard-level-in-level-scale crime sites copying login login pages, these scam pages look like product or support zones.
Reports added that some of them always work and are still collecting sensitive data, and some are in standby for future use.
Investigators find that almost all families who are imprisoned in this operation has led to one IP address – 185.208.1556.66. This server works as a campaign HUB, managing stolen credentials, linking taskwork, and fraud.
Picture entered from Unscurcuch, chart from trade transaction

Process of planning In BitCoinist focuses on delivery, accurate, accurate content, and unlimited content. We support solid Sourcing levels, and each page actively receives updates by our team specialist and informative editories. This process ensures integrity, compliance, and the number of our students’ content.



